Cybersecurity researchers are calling attention to the “democratization” of the phishing ecosystem as Telegram has become the epicenter of cybercrime, allowing threat actors to launch mass attacks for as little as $230. This is not the first time the popular messaging platform has come under the radar for facilitating malicious activity, in part due to lenient moderation efforts.
As a result, what used to be available in invitation-only forums on the dark web is now easily accessible through public channels and groups, opening the doors of cybercrime to eager and inexperienced cybercriminals.
One of the malicious Telegram bots is Telekopye, which can create fake web pages, emails and SMS messages to help threat actors carry out large-scale phishing scams.
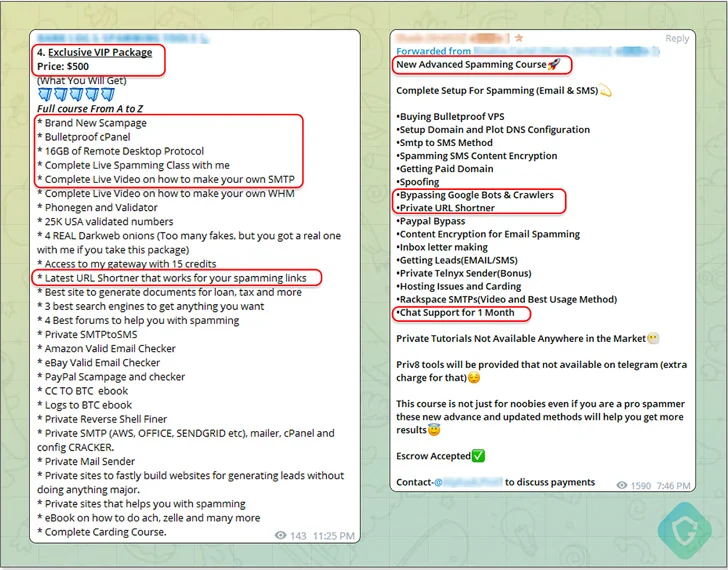
Backdoor mails marketed in various Telegram groups are PHP scripts injected into already infected but legitimate websites to send persuasive emails using the legitimate domain of the exploited website to bypass spam filters.
To further increase the likelihood of success of such campaigns, digital marketplaces on Telegram also provide what are known as “letters” that make email messages appear genuine in order to trick victims into clicking on them. Fake link pointing to the scam page.
Telegram also hosts aggregated data sets containing valid and relevant email addresses and phone numbers to target. These contacts, referred to as “leads”, are sometimes “enriched” with personal information such as names and physical addresses to maximize impact.



